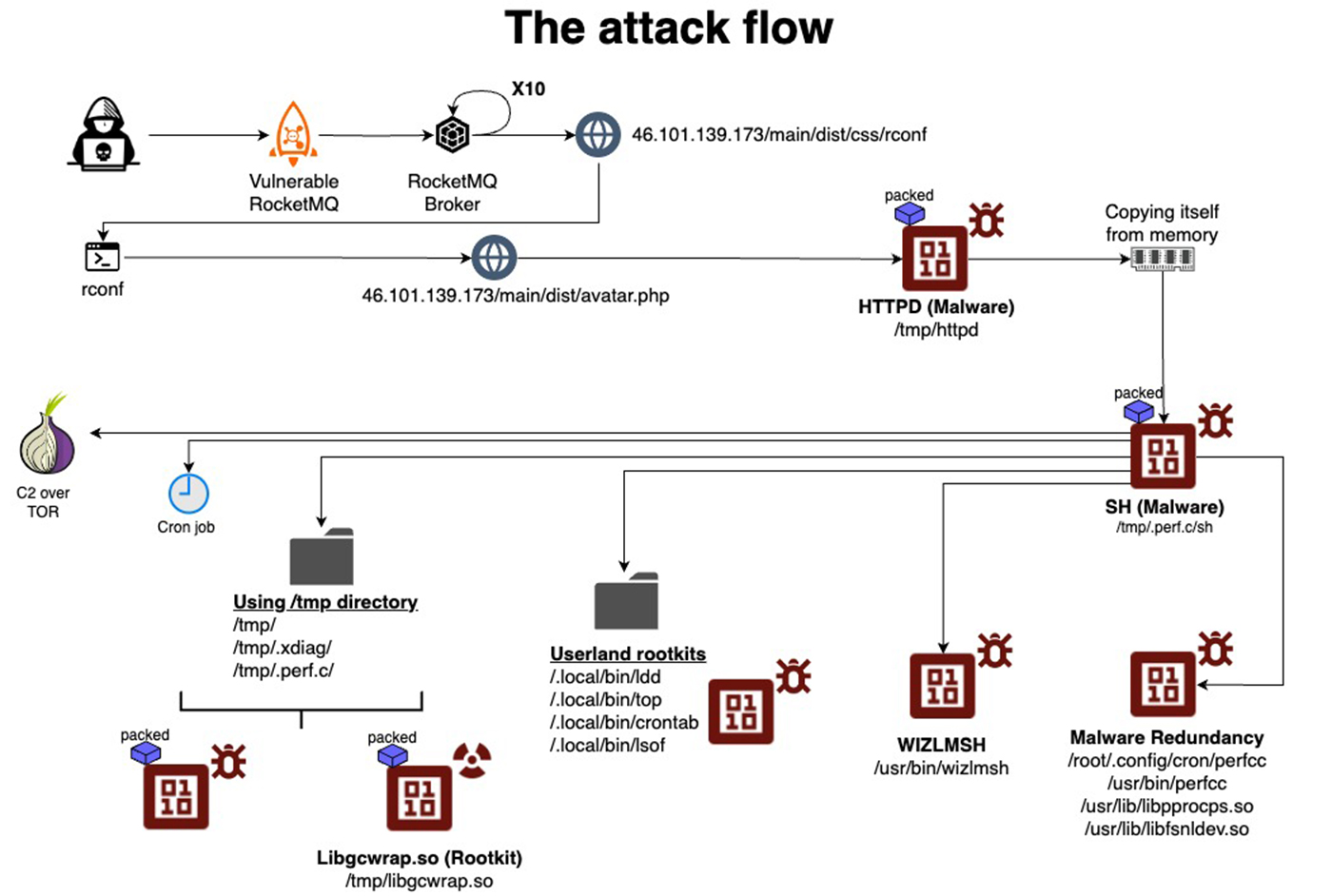
Linux systems have been under threat from a sophisticated malware known as Perfctl since 2021. This malware exploits over 20,000 common misconfigurations and severe vulnerabilities, such as CVE-2023-33426 in Apache RocketMQ, making potentially millions of Linux-based systems vulnerable to attacks.
Perfctl employs various stealth techniques to avoid detection. These include mimicking common Linux process and file names, installing as rootkits, and using Unix sockets over TOR for external communications. Additionally, it manipulates the Linux process pcap_loop to evade admin tools and suppresses error messages that could alert users to its presence.
The persistence mechanisms of Perfctl are particularly alarming. It modifies the ~/.profile script and copies itself across multiple disk locations to survive reboots and removal attempts. This malware not only mines cryptocurrency using the resources of the infected machine but also turns it into a proxy for illicit internet traffic, which could include other forms of cyberattacks such as data exfiltration and the deployment of additional malware payloads.
Detection can be challenging due to its stealthy nature, but some signs include unexpected 100% CPU utilization alerts from monitoring setups, which cease when a user logs in via SSH or console. Searching the system for unfamiliar process names similar to ‘perfcc’ or ‘perfctl’ that appear to restart on their own could also indicate infection. Despite its detection by some antivirus software, the malware’s ability to consistently restart and evade complete removal has been a significant challenge.
To read more about this ongoing security threat, visit Ars Technica’s detailed report.