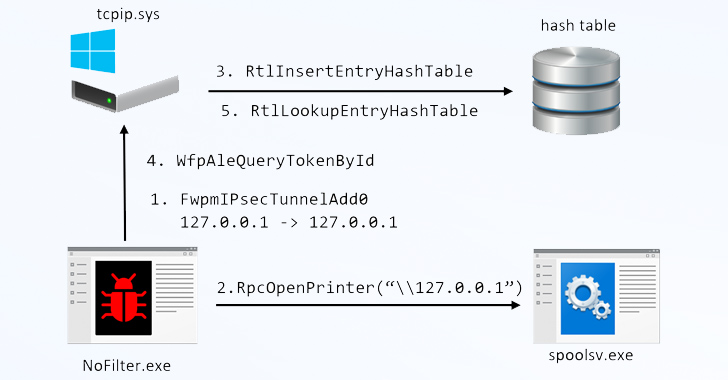
A new attack method, NoFilter, has been discovered that exploits the Windows Filtering Platform (WFP) to escalate privileges in the Windows operating system. Revealed at the DEF CON security conference, the technique allows malware to duplicate access tokens of other processes, launching a child process with SYSTEM privileges. This stealthy method leaves minimal evidence, highlighting the potential for new attack vectors within built-in OS components. The discovery follows revelations of other novel attack approaches, including cloud-based ransomware and a “threadless” process injection technique.
Read more at The Hacker News…